AES256-GCM-10G25G IP Core Datasheet

Core Facts |
|
|
Provided with Core |
|
|
Documentation |
User Guide, Design Guide |
|
Design File Formats |
Encrypted File |
|
Instantiation Templates |
VHDL |
|
Reference Designs & Application Notes |
Vivado Project, Quartus Project, See Reference design manual |
|
Additional Items |
Demo on KCU116 |
|
Support |
|
|
Support Provided by Design Gateway Co., Ltd. |
|
Design Gateway Co., Ltd
E-mail: ip-sales@design-gateway.com
URL: design-gateway.com
Features
· Support AES-GCM mode standard.
· Support 128/256-bit key size, 96-bit iv size.
· Support zero-length AAD or data input.
· Peak throughput rate at 128 Mbits/MHz.
· Speed up to 38.4 Gbps @300MHz.
Table 1 Example Implementation Statistics
|
Family |
Example Device |
Fmax (MHz)
|
CLB Regs
|
CLB LUTs
|
CLB/Slice1 |
IOB |
BRAMTile |
Design Tools |
|
Zynq-Ultrascale+2 |
xczu7ev-ffvc1156-2-e |
290 |
5096 |
19175 |
3497 |
- |
- |
Vivado2022.1 |
|
Kintex UltraScale+ |
xcku5p-ffvb676-2-e |
300 |
5096 |
19276 |
3512 |
- |
- |
Vivado2022.1 |
|
Virtex-Ultrascale+2 |
xcvu9p-flga2104-2L-e |
300 |
5096 |
19291 |
3560 |
- |
- |
Vivado2022.1 |
|
xcvc1902-vsva2197-2MP-e-S |
275 |
5095 |
19357 |
3432 |
- |
- |
Vivado2022.1 |
Notes:
1) The actual logic resource depends on the percentage of unrelated logic.
2) The results were obtained from implementation in the same environment, but have not been tested on the actual board.
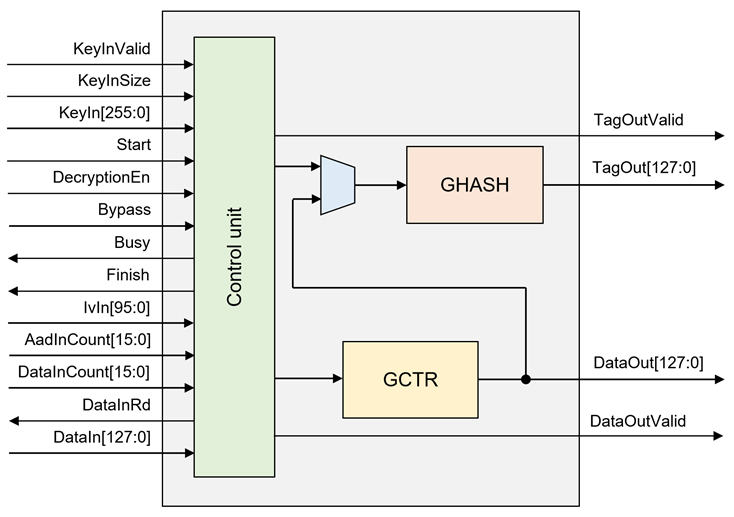
Figure 1 AES256GCM10G25G-IP Block Diagram
General Description
AES256-GCM-10G25G IP Core, called AESGCM-IP, implement the advanced encryption standard (AES) in Galois/Counter Mode (GCM) which is widely used for Authenticated Encryption with Associated Data (AEAD) application, including IPSEC, MACSEC and TLS (Transport Layer Security) versions 1.2 and 1.3. Additionally, AES-GCM is used in fiber channel communications and storage applications.
AESGCM-IP operates with a 96-bit Initialization Vector (IV) and supports either a 256-bit or 128-bit AES key, depending on user configuration. It can provide confidentiality and data authentication by using Additional Authenticated Data (AAD) and authentication tag. It is designed to support zero-length plaintext/ciphertext input which is the special case of GCM mode, called GMAC, and also support zero-length AAD.
There are 2 main operations in AES-GCM: encryption/decryption by GCTR and tag calculation by the GHASH algorithm. AESGCM-IP can operate 128-bit data every clock cycle, as a result, it can operate at speeds up to 38.4Gbps at 300MHz, which can be used effectively on 10G/25G Ethernet.
Functional Description
AESGCM-IP interface signals can be divided into three parts as follows: key setting signals, parameter setting signals, and data control signals.
Table 2 Interface signals of AESGCM-IP
|
Signal name |
Dir |
Description |
|
RstB |
In |
IP core system reset. Active low. |
|
Clk |
In |
IP core system clock. |
|
version[31:0] |
Out |
32-bit version number of AESGCM-IP. |
|
Key setting signals |
||
|
KeyInValid |
In |
Specifies the validity of KeyInSize and KeyIn. Assert to ‘1’ to set up KeyInSize and KeyIn into AESGCM-IP. Start is ignored if KeyInValid is ‘1’. |
|
KeyInSize |
In |
Specifies the KeyIn size: ‘0’ for 128-bit and ‘1’ for 256-bit. Must be valid when KeyInValid is asserted. |
|
KeyIn[255:0] |
In |
256-bit key for AES in CTR mode. For 128-bit mode (KeyInSize=‘0’), KeyIn[255:128] is used; for 256-bit mode (KeyInSize=‘1’), KeyIn[255:0] is used. Must be valid when KeyInValid is asserted. |
|
Parameter setting signals |
||
|
Start |
In |
User signal to start AESGCM-IP operation. |
|
DecryptionEn |
In |
Specifies encryption mode: ‘0’ for encryption, ‘1’ for decryption. Must be valid during operation. |
|
Bypass |
In |
Specifies bypass mode: ‘0’ for encryption/decryption, ‘1’ for bypass mode. Must be valid during operation. |
|
Busy |
Out |
Specifies the busy status of operation. Start and KeyInValid are ignored if Busy is ‘1’. |
|
Finish |
Out |
Specifies the finish status of AESGCM-IP. Assert to ‘1’ at the last cycle of operation. |
|
IvIn[95:0] |
In |
96-bit IV data for AES block cipher in CTR mode of operation. |
|
AadInCount[15:0] |
In |
The number of AAD in bytes. Must be valid during operation. |
|
DataInCount[15:0] |
In |
The number of input data in bytes. Must be valid during operation. |
|
Data control signals |
||
|
DataInRd |
Out |
Control signal to read DataIn, which will be asserted around 13~17 clock cycles after Start becomes ‘1’. |
|
DataIn[127:0] |
In |
128-bit input data, including AAD and data. Must be valid when DataInRd is asserted. |
|
DataOutValid |
Out |
Specifies output data valid. Asserts ‘1’ when DataOut is valid (cipher text for encryption, plain text for decryption). |
|
DataOut[127:0] |
Out |
128-bit output data. Valid when DataOutValid is asserted. |
|
TagOutValid |
Out |
Specifies tag valid. Assert to ‘1’ when tag calculation is done. |
|
TagOut[127:0] |
Out |
128-bit output tag. Valid when TagOutValid is asserted. |
AESGCM-IP operation is as simple as 3 steps to use as below.
· Key setting
The key setting is the first step in using AESGCM-IP. As shown in Figure 2, AESGCM-IP is configured with KeyIn[255:128] when KeyInValid=‘1’ and KeyInSize=‘0’ for a 128-bit key, and with KeyIn[255:0] when KeyInValid=‘1’ and KeyInSize=‘1’ for a 256-bit key. After that, this KeyIn will be used for every encryption operation, and it can be changed by asserting KeyInValid to ‘1’.

Figure 2 AESGCM-IP timing diagram in key setting
· Parameter setting
After key setting, AESGCM-IP starts the process when Start is asserted to ‘1’. DecryptionEn, Bypass, IvIn, AadInCount and DataInCount must be valid when Start=‘1’ and be hold during operation. User can set DecryptionEn to ‘0’ and Bypass to ‘0’ for operating in encryption mode as shown in Figure 3 or set DecryptionEn to ‘1’ and Bypass to ‘0’ for operating in decryption mode as shown in Figure 4. And set Bypass to ‘1’ for operating in Bypass mode as shown in Figure 5.

Figure 3 AESGCM-IP timing diagram in encryption mode
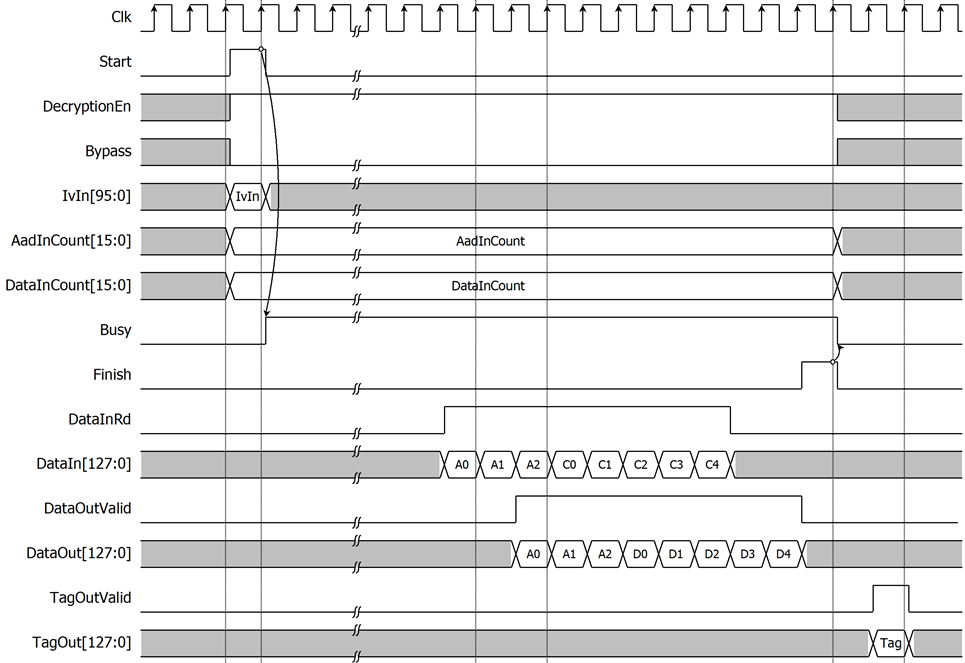
Figure 4: AESGCM-IP timing diagram in decryption mode

Figure 5: AESGCM-IP timing diagram in Bypass mode
For the best performance of process, Figure 6 shows the timing diagram of continuous and pipelining process. User can use Finish signal as a trigger signal for setting new parameters and sending new start command in next cycle.
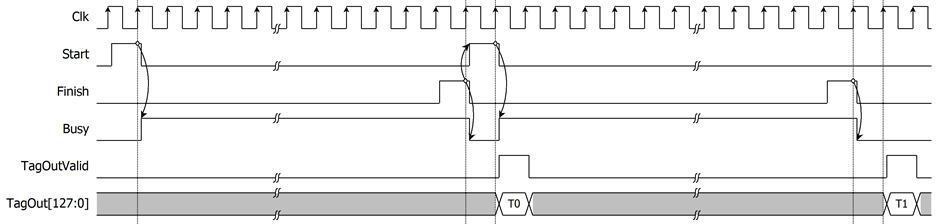
Figure 6: Continuous and pipelining operation
· Data control
According to DataIn width is 128 bits (16 bytes) and AESGCM-IP is designed to read DataIn every clock cycle when AESGCM-IP is ready to start encryption/decryption process. After Start is set to begin the operation, user must prepare first valid DataIn[127:0]. Then user can use DataInRd signal as a trigger signal for setting the next DataIn continuously. If AadInCount is not aligned to 128 bits (16 bytes), the last 128-bit AAD must be right-padded with zeros.

Figure 7: DataIn arrangement for 30-byte AAD and 15-byte data
Figure 7 is a detailed example of 30-byte AAD and 15-byte data preparation. DataIn0, DataIn1 and DataIn2 is represent as DataIn[127:0] in the first, second and third clock cycle respectively. The first 16-byte of AAD (AADBytes0-AADBytes15) is set as DataIn0[127:120], ..., DataIn0[7:0]. The remained 14-byte of AAD (AADBytes16-AADBytes29) is set as DataIn1[127:120], ..., DataIn1[23:16] and DataIn1[15:0] must be zeros. Then the remained 15-byte data (DATABytes0-DATABytes14) must be set as DataIn2[127:8].
As shown in Figure 3 and Figure 4, at last operation cycle, the Finish signal is asserted to ‘1’ and Busy signal is cleared to ‘0’ in the next cycle. TagOutValid is active only one clock on the next clock after Busy is cleared to ‘0’. In case of Bypass mode is active as shown in Figure 5, the TagOut is not calculated and TagOutValid is not active.
Verification Methods
The AES256-GCM-10G25G IP Core functionality was verified by simulation and also proved on real board design by using KCU116 development boards.
Recommended Design Experience
The user must be familiar with HDL design methodology to integrate this IP into a system.
Ordering Information
This product is available directly from Design Gateway Co., Ltd. Please contact Design Gateway Co., Ltd. For pricing and additional information about this product, use the contact information on the front page of this datasheet.
Revision History
|
Revision |
Date (D-M-Y) |
Description |
|
2.01 |
1-Nov-24 |
- Add more detailed condition of signals. - Revise wording. |
|
2.00 |
8-Oct-24 |
- Enhance to support 128-bit key. |
|
1.04 |
23-Feb-23 |
- Add Bypass feature. - Improve performance. - Add more resource information. |
|
1.03 |
27-Sep-22 |
Update pictures and description. |
|
1.02 |
20-Sep-22 |
New design to improve performance. |
|
1.00 |
21-Jun-22 |
New release. |