AES256XTSSTGIP Demo Instruction
2 FPGA development board setup
4 Command detail and testing result
4.3 Set encryption/decryption IV
This document describes the instruction to demonstrate the operation of AES256XTSSTGIP on FPGA development boards. In the demonstration, AES256XTSSTGIP are used to encrypt and decrypt data between two memories in FPGA. User can fill memory with plain or cipher data patterns, set encryption key, tweakable key, Initialization Vector (IV) and control test operation via serial console.
1 Environment Setup
To operate AES256XTSSTGIP demo, please prepare following test environment.
1) FPGA development board
Versal Premium Series VPK120 Evaluation Kit or
Versal AI Core Series VCK190 Evaluation Kit
2) Test PC.
3) JTAG connection connecting between FPGA boards and Test PC
Micro USB cable for VPK120 or
USB type-C cable for VCK190 board.
4) Vivado tool for programming FPGA installed on Test PC.
5) Serial console software such as TeraTerm installed on Test PC. The setting on the console is Baudrate=115200, Data=8-bit, Non-parity and Stop=1.
6) Batch file named “AES256XTSSTG4XIPTest.bat” or “AES256XTSSTG2XIPTest.bat” (To download these files, please visit our web site at www.design-gateway.com)

Figure 1‑1 AES256XTSSTG4XIP demo environment on VPK120 board
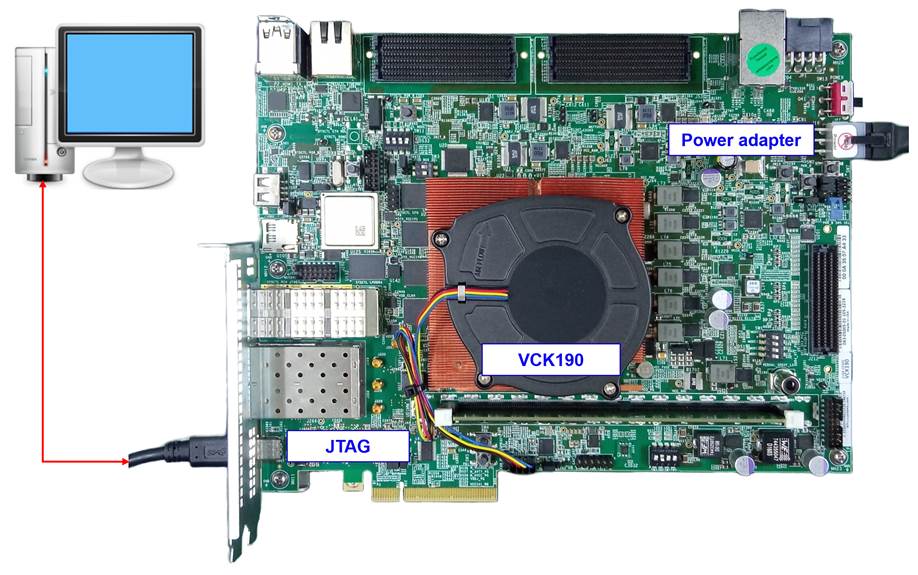
Figure 1‑2 AES256XTSSTG2XIP demo environment on VCK190 board
2 FPGA development board setup
1) Make sure power switch is off and connect power supply to FPGA development board.
2) Connect USB cables between FPGA board and PC via micro USB port for VPK120 or USB type-C port for VCK190.
3) Power on system.
4) Download configuration file and firmware to FPGA board by following step,
a) open Vivado TCL shell.
b) change current directory to download folder which includes demo configuration file.
c) Type “AES256XTSSTG4XIPTest.bat” or “AES256XTSSTG2XIPTest.bat”, as shown in Figure 2-1.

Figure 2‑1 Example command script for download configuration file
3 Serial Console
User can fill RAMs with plain data or cipher data patterns, set encryption key, set tweakable key, IV and control test operation via the serial console. When configuration is completed, AES256XTSSTGdemo command menu will be displayed as shown in Figure 3‑1. The detailed information of each menu is described in topic 4.

Figure 3‑1 Serial console
4 Command detail and testing result
Step to set encryption key as follows
a) Select “1. Set rEncEKeyIn and rDecEKeyIn”.
b) Current rEncEKeyIn will be displayed on serial console as shown in Figure 4‑1.
c) Set new rEncEKeyIn: User is allowed to input new key in hex format or press “enter” to skip setting new key. Then the current encryption key is printed again.
d) Current rDecEKeyIn key will be displayed on serial console.
e) Set new rDecEKeyIn key: User is allowed to input new key in hex format or press “enter” to use rEncEKeyIn as rDecEKeyIn. Then the current decryption key is printed again.
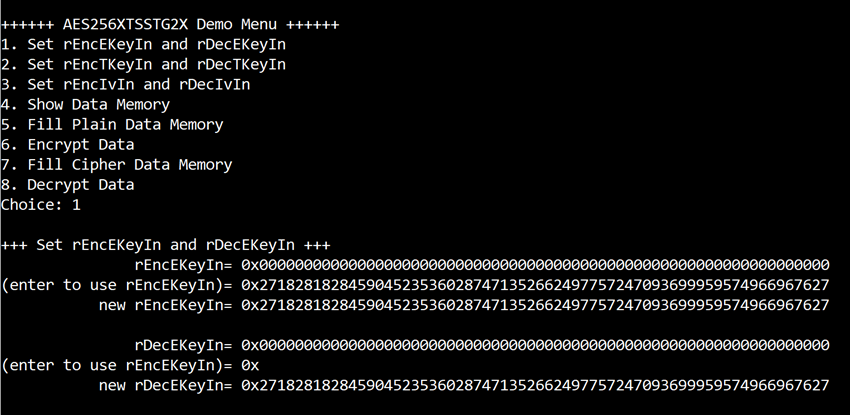
Figure 4‑1 Set rEncEKeyIn and rDecEKeyIn example
Step to set tweakable key as follows
a) Select “2. Set rEncTKeyIn and rDecTKeyIn”.
b) Current rEncTKeyIn will be displayed on serial console as shown in Figure 4‑2.
c) Set new rEncTKeyIn: User is allowed to input new key in hex format or press “enter” to skip setting new key. Then the current encryption key is printed again.
d) Current rDecTKeyIn will be displayed on serial console.
e) Set new rDecTKeyIn: User is allowed to input new key in hex format or press “enter” to use rEncTKeyIn as rDecTKeyIn. Then the current decryption key is printed again.
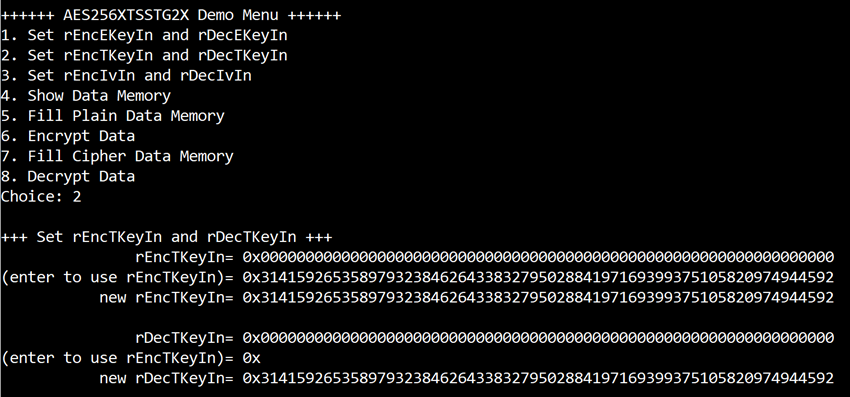
Figure 4‑2 Set rEncTKeyIn and rDecTKeyIn example
4.3 Set encryption/decryption IV
Step to Set encryption/decryption IV as follows
a) Select “3. Set rEncIvIn and rDecIvIn”.
b) Current rEncIvIn will be displayed on serial console as shown in Figure 4‑3.
c) Set new rEncIvIn: User is allowed to input new IV in hex format or press “enter” to skip setting new key. Then the current encryption IV is printed again.
d) Current rDecIvIn will be displayed on serial console.
e) Set new rDecIvIn: User is allowed to input new IV in hex format or press “enter” to use rEncIvIn as rDecIvIn. Then the current decryption IV is printed again.

Figure 4‑3 Set rEncIvIn and rDecIvIn example
4.4 Show Data Memory
To show data in memory, user can select “4. Show Data Memory” and input the desired number of 512-byte data to show. Both plain data and cipher data will be displayed in table-form as shown in Figure 4‑4. User have the option to press “enter” to use the default value.
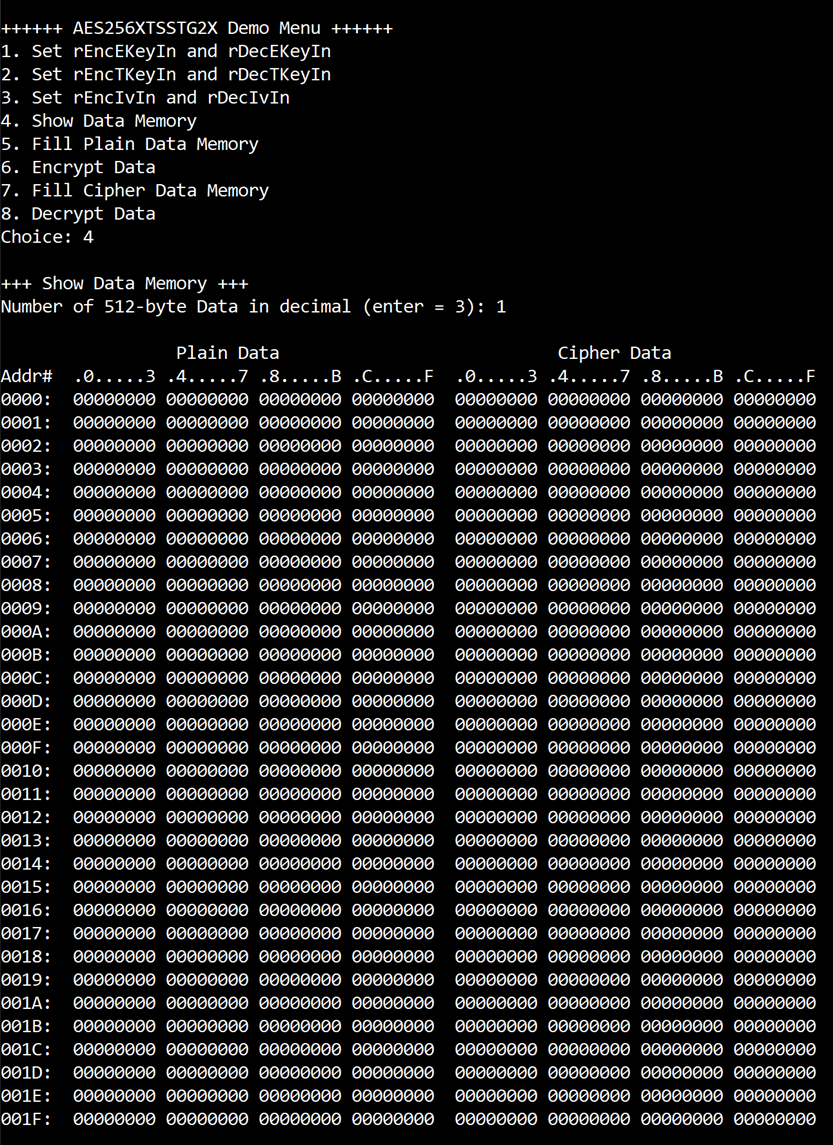
Figure 4‑4 Displayed Data example
4.5 Fill Plain Data Memory
Step to fill plain data in memory as follows
Select “5. Fill Plain Data Memory”.
Input the desired number of 512-byte data. User can press “enter” to use the default value of plain data. user can a select data pattern.
There are four pattern to fill memory.
a. zero pattern
b. 8-bit counter
c. 16-bit counter
d. 32-bit counter
Whole plain data memory is filled with selected data pattern.

Figure 4‑5 Displayed Data when select pattern
4.6 Encrypt
Step to encrypt data as follows
a) Select “6. Encrypt” to encrypt plain data in memory.
b) Input parameter for Iv Increment.
c) When the encryption process is finished, both plain data and cipher data will be displayed in table-form as shown in Figure 4‑6.
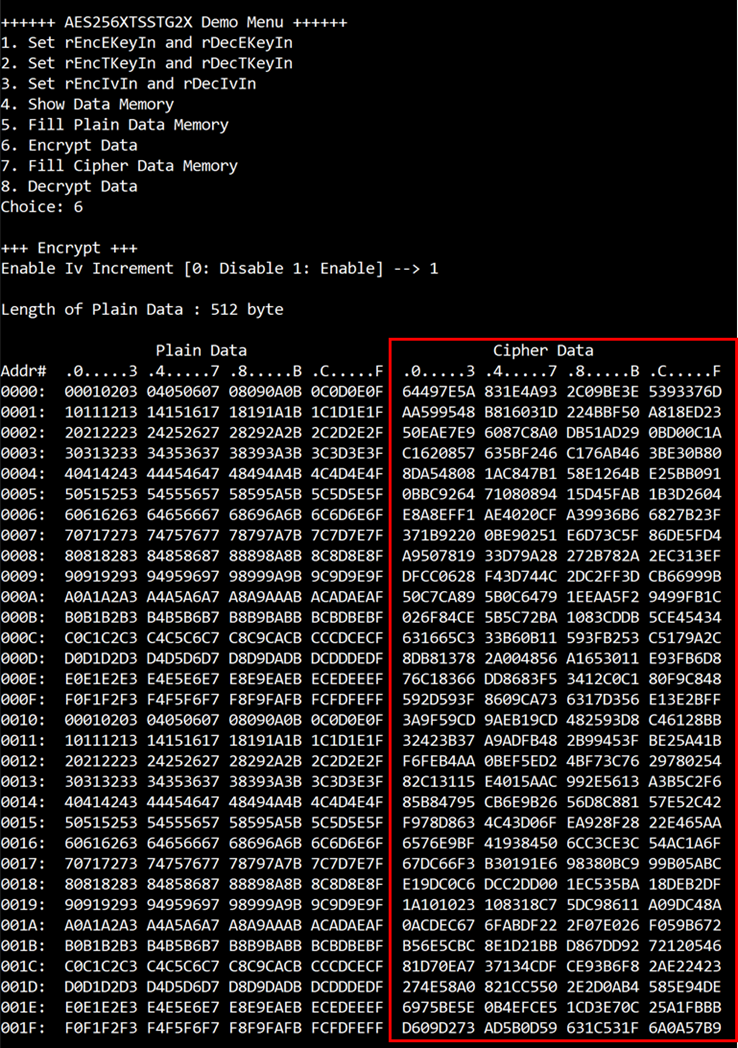
Figure 4‑6 Serial console after finished encryption process
4.7 Fill Cipher Data Memory
Step to fill Cipher data in memory as follows
a) Select “7. Fill Cipher Data Memory”.
b) Input the desired number of 512-byte data. User can press “enter” to use the default value of Cipher data. user can select data pattern.
c) There are four pattern to fill memory.
a. zero pattern
b. 8-bit counter
c. 16-bit counter
d. 32-bit counter
d) Whole cipher data memory is filled with selected data pattern.
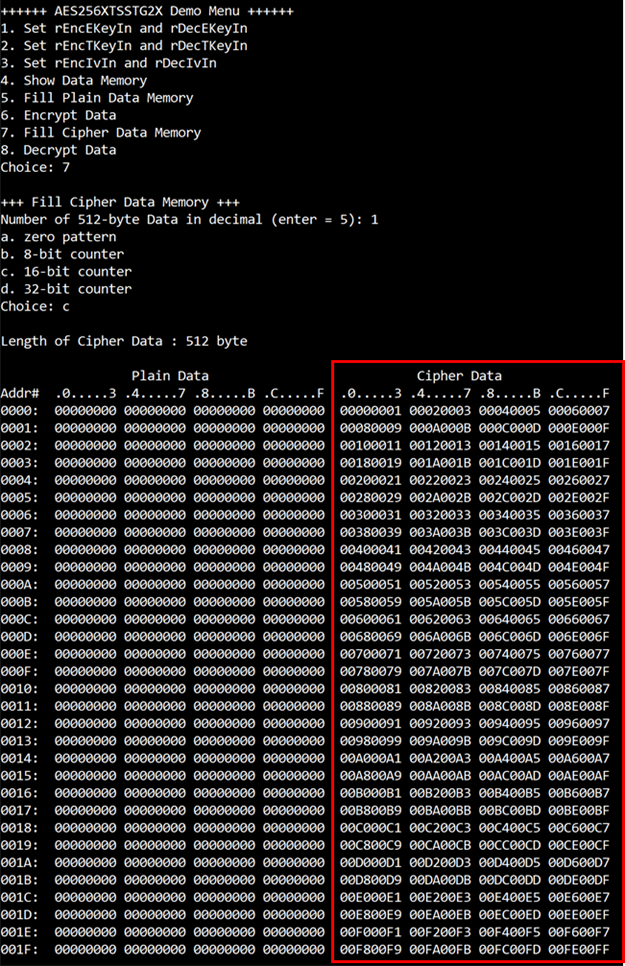
Figure 4‑7 Displayed Data when select pattern
4.8 Decrypt
Step to decrypt data as follows
a) Select “8. Decrypt Data” to decrypt cipher data in memory.
b) Input parameter for Iv Increment.
c) When the decryption process is finished, both plain data and cipher data will be displayed in table-form as shown in Figure 4‑8.

Figure 4‑8 Serial console after finished decryption process
5 Revision History
|
Revision |
Date |
Description |
|
1.01 |
9-May-2024 |
Add detailed instruction for VPK120 demo |
|
1.00 |
25-Aug-2023 |
Initial version release |