Enhancing TLS Data Security and Performance with DG’s TLS1.3 IP-Core

Join us as we delve into the world of Transport Layer Security (TLS). In this article, Discover the importance of TLS, its role in securing connections, and how it works. We explore the TLS1.3 protocol, which offers enhanced encryption, authentication, and integrity to safeguard sensitive information from potential hackers.
Learn about the risks of unsecured connections and how TLS mitigates them, preventing interception and tampering of data.
We also introduce a hardware solution by DG that optimizes TLS1.3 performance, improving transfer speed and offloading CPU tasks.
What is TLS?
TLS stands for Transport Layer Security. It is a security protocol used to establish a secure connection between two devices over the internet. It’s an upgraded version of the SSL or Secure Sockets Layer, and it provides encryption, authentication, and integrity to protect sensitive information from hackers.
TLS is widely used in email, secure web browsing, file transferring, voice-over-IP, etc.
Why TLS is important?
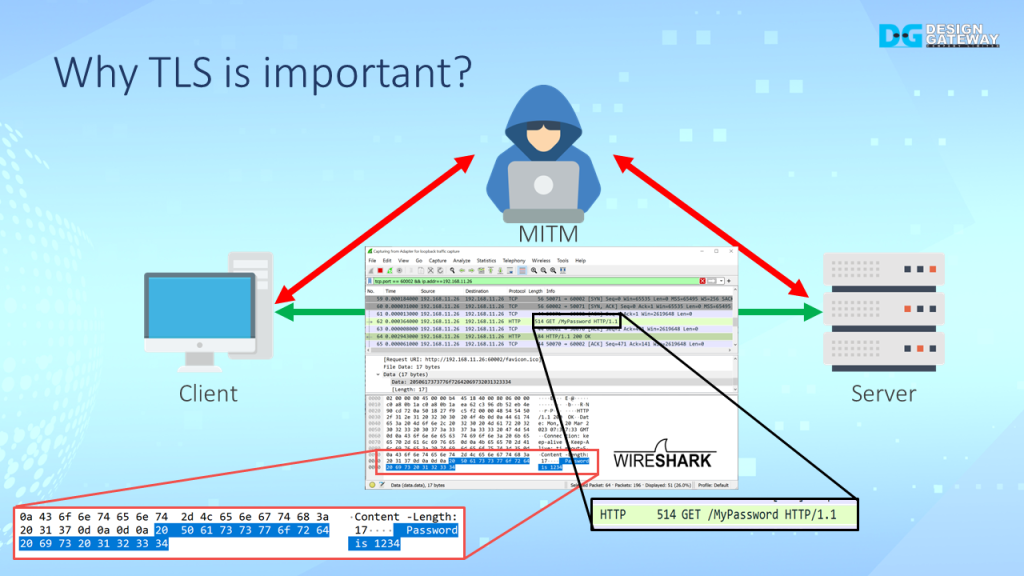
When using unsecured connections such as HTTP, data is transported between the client and server in plain text using the Transmission Control Protocol (TCP).
This makes it easy for a potential attacker to intercept and capture the packets using network tools like Wireshark. This means that sensitive data or privacy can be compromised.
Additionally, a man-in-the-middle attack can be carried out, where an attacker can modify the packets being transmitted.
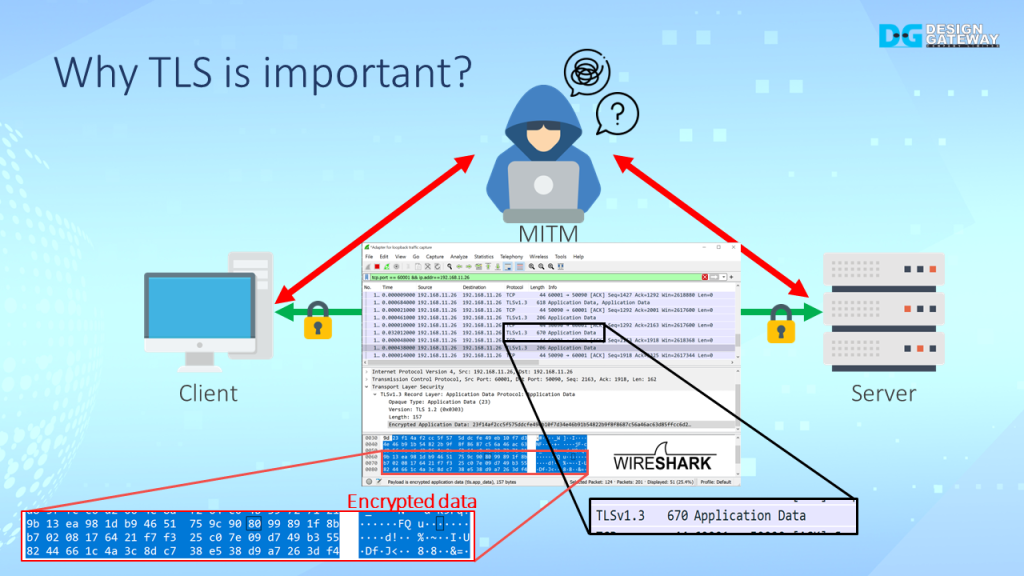
By using TLS, the data is encrypted and secured before being transported between the client and server. This makes it much more difficult for a potential attacker to intercept and read the data.
Additionally, the use of digital certificates provides a mechanism for verifying the identity of the server, helping to prevent man-in-the-middle attacks.
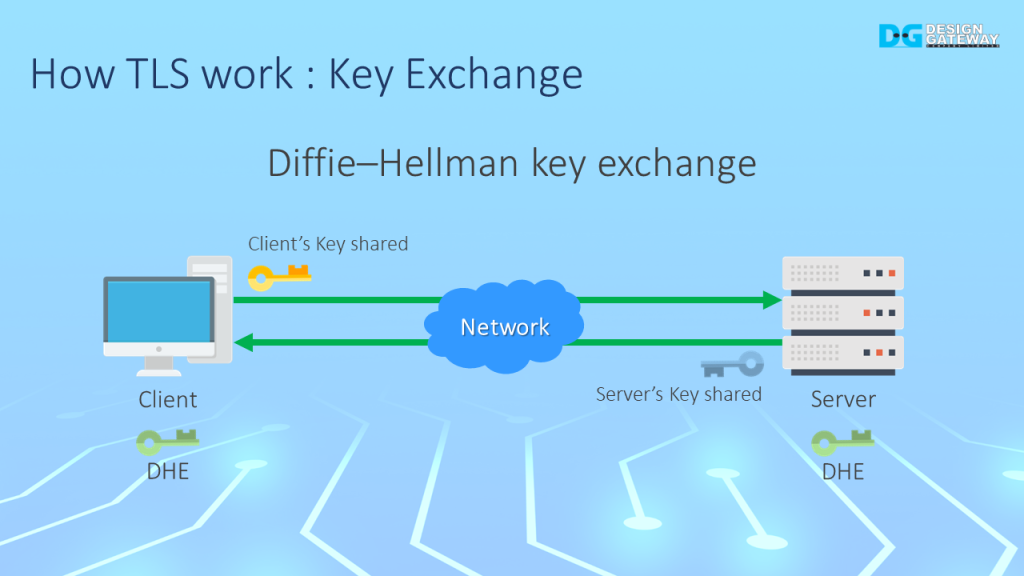
When using TLS for secure communication, the symmetric encryption algorithm requires both the client and the server to exchange a shared secret key.
In TLS 1.3, the Diffie-Hellman algorithm is used to generate a shared secret key. This algorithm works by using a mathematical formula to generate a shared secret that can be used for the encryption and decryption of messages.
After the shared secret key is generated, both the client and the server compute and derive the Diffie-Hellman ephemeral (DHE) key material. This key material is then used for key derivation and encryption/decryption of messages.
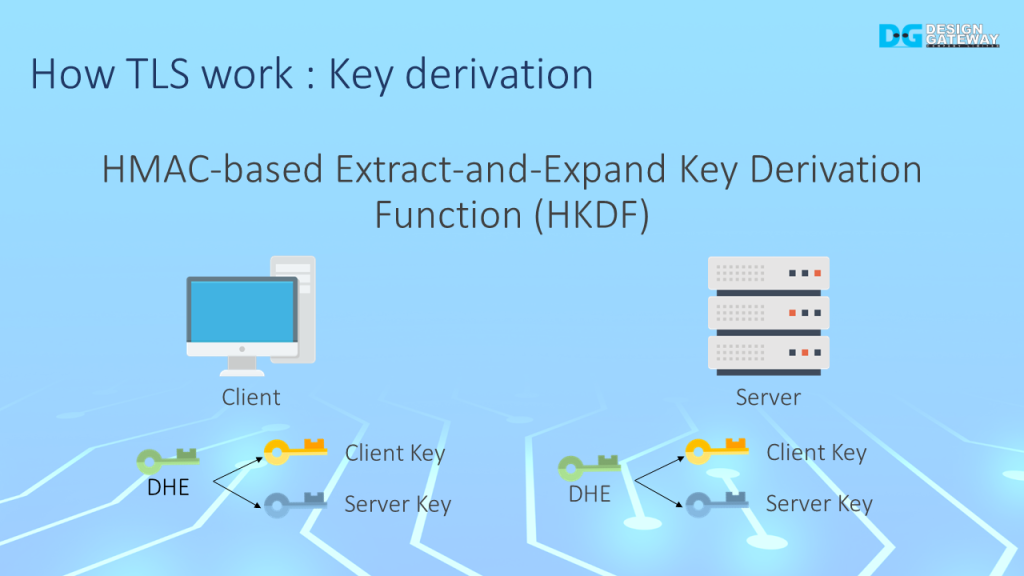
Diffie-Hellman ephemeral (DHE) key material will be used to derive the session key. Both the client and server use HMAC-based Extract-and-Expand Key Derivation or HKDF to derive the same keys, Client key and Server key.
The client key will be used to encrypt or decrypt messages sent from the client to the server, while the server key will be used to encrypt or decrypt messages sent from the server to the client.
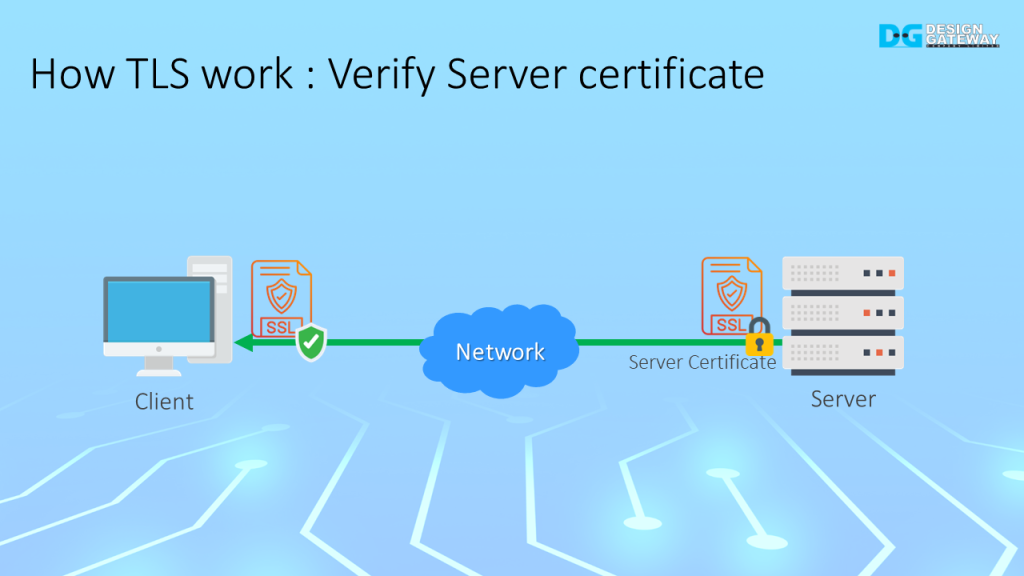
To establish a secure TLS connection, the client must verify the server’s SSL certificate, which is done using the RSA algorithm.
The SSL certificate authenticates the website’s identity and ensures that the handshake message sent before is from the server.
The server sends the SSL certificate and its signature to the client. Then the client verifies the signature by using the public key in the certificate. If the certificate is invalid, the TLS connection will be terminated to prevent communication with an untrustworthy source.
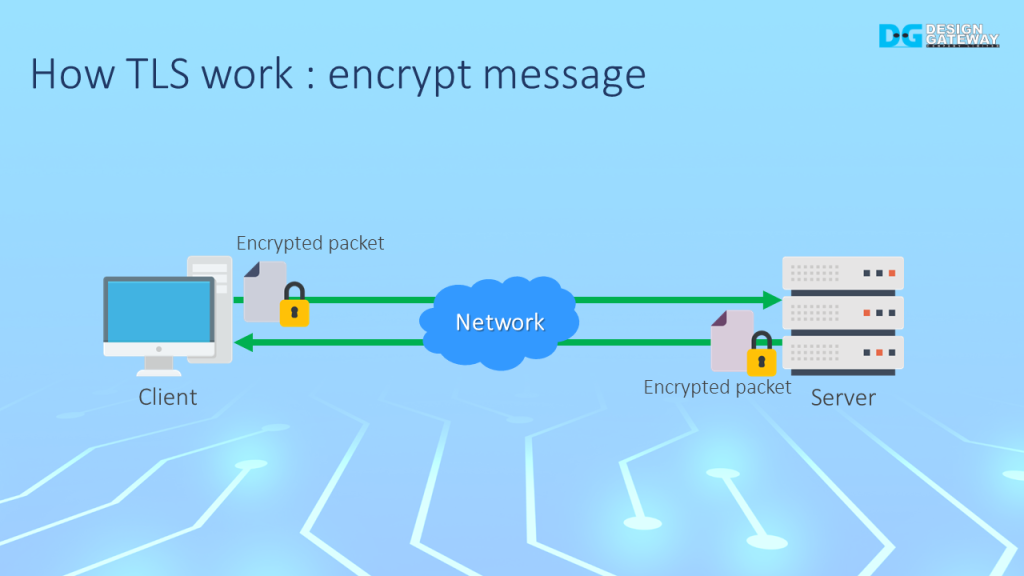
After the key exchange, all packets in the handshake phase and data transfer phase are encrypted with the AES-GCM algorithm.
The packet contains Additional Authenticated Data (AAD), an encrypted message, and an authentication tag. It can provide confidentiality and data authentication by comparing the authentication tag from the packet with the tag generated by the receiver.
If the authentication tag and tag generated by the receiver do not match. It can be assumed that the encrypted message is modified before sending it to receiver.
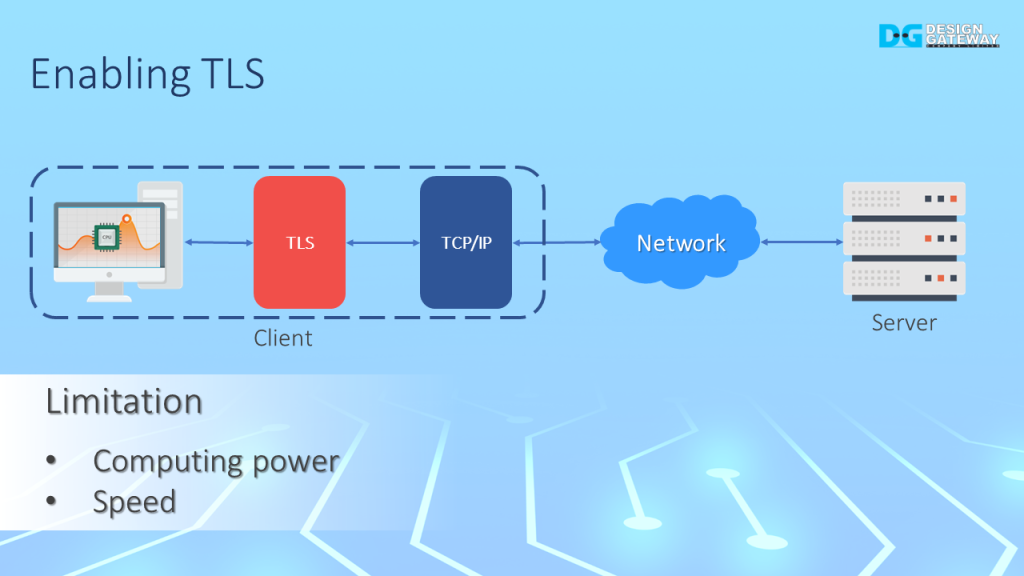
For a secure connection, TLS is implemented over TCP/IP, with cryptographic algorithms used for handshaking and transferring data.
However, the computing power and speed of the controller may be a limitation.
Handshaking, encrypting data before sending, and decrypting it upon receiving will cause overhead time and reduce the throughput of the transfer, particularly in low-performance controllers.
In these cases, the CPU may be consumed at 100% and unable to handle any other tasks.

To address these limitations, DG provides a hardware solution for TLS 1.3.
This solution is easy to use and compatible with servers, and it can recover transfer speed to achieve maximum throughput.
Additionally, it functions as an offload engine, allowing the CPU to handle other tasks.
For more information about our TLS 1.3 solution, please visit https://dgway.com/ASIP_E.html
Youtube: https://youtu.be/1ZZiC-T4s9M
Article about TLS1.3